As Secunnix Red Team, we will try to tell you about a work we have done recently. The study we started on a Foundation University reveals the extent to which Cyber Security rules are complied with. If you will have a better understanding of what kind of bad results it will have with this article, most systems in our country ignore the rules of open information gathering, which seem small but actually form the main framework for hacking.
What is open source information gathering?
Secunnix Red Team In short, all data about the system to be attacked, from which the attacker can directly compile information. To explain in detail;
Email address, phone number, etc. of an authorized or unauthorized person on a public website,
The directories left open on the website to be attacked,
Social media accounts,
Information that was hacked and shared on the internet before (password, name, surname, e-mail address, etc.)
Using open source information
As the Secunnix team, we started to scan the main domain and subdomains connected to the main domain as a whole. We found a script that manages the transfer process of students from other universities to this university. In this script, something caught our eye in the username and login section,
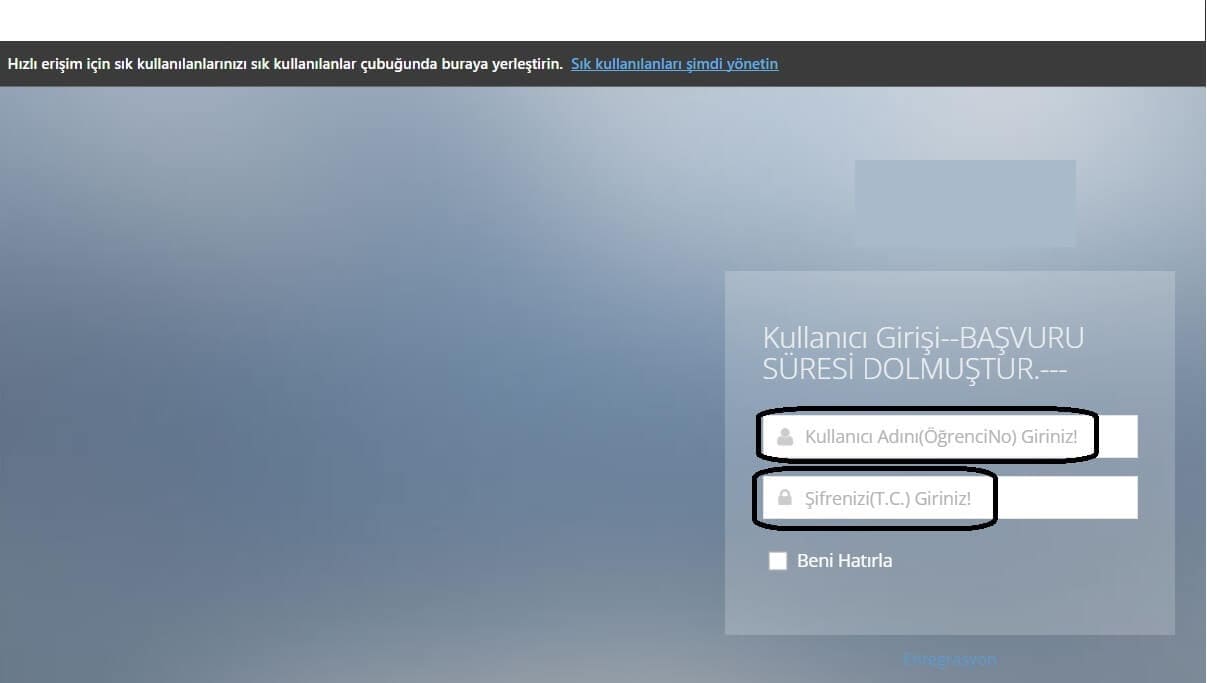
Yes, as you can see in the picture; The user name information was Student Number, and the password information was T.C Identity Number. The information we could access from this vulnerability would have defined us the authorization to access the system. We have detected that directory listing is turned on on another subdomain of the target and student information is accessible in the directories.
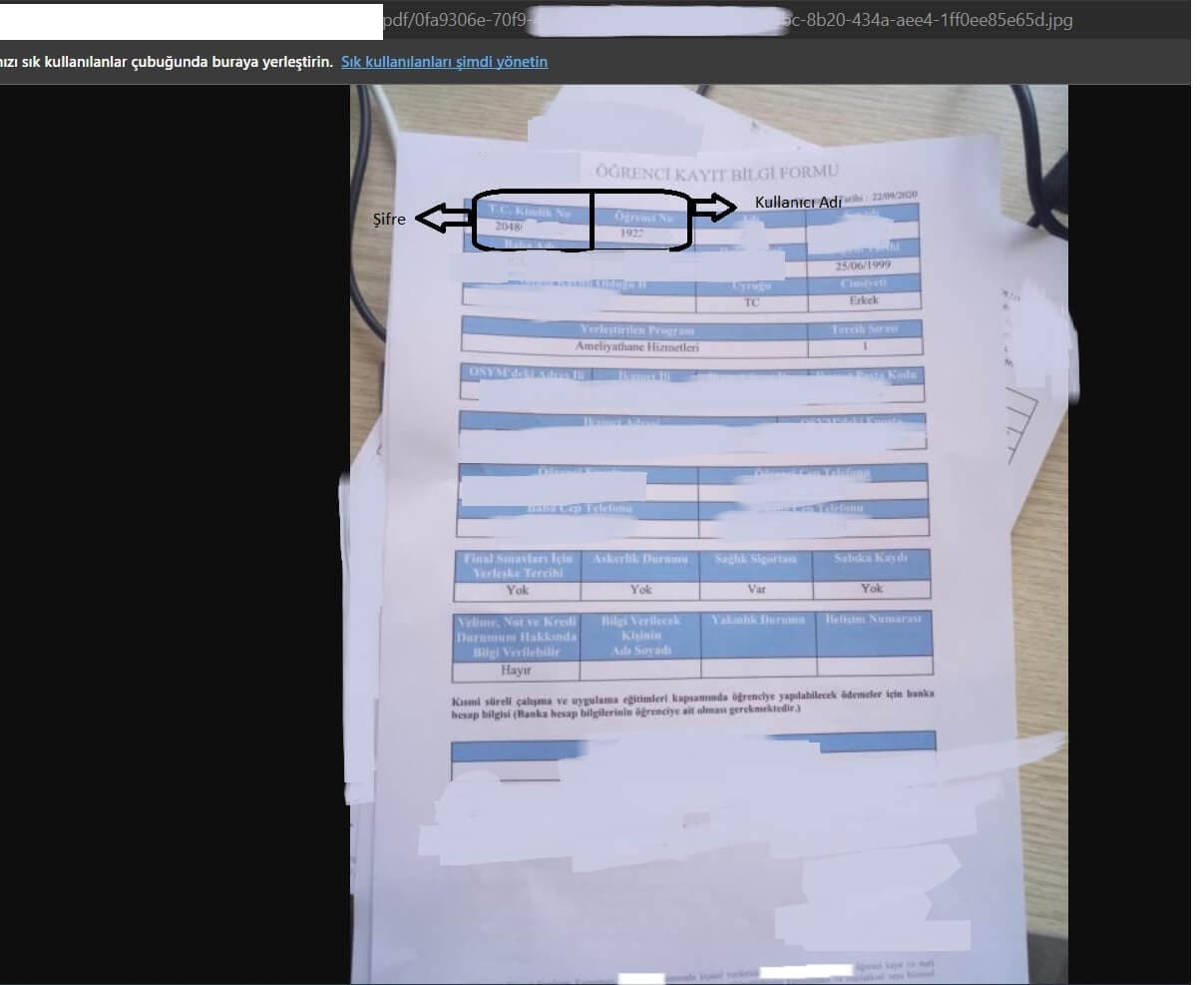
Thanks to this document we found, we were able to log in to the system since we had a Student ID and TR Identity Number. After logging into the system, we encountered an upload form where students could upload some documents such as petitions.
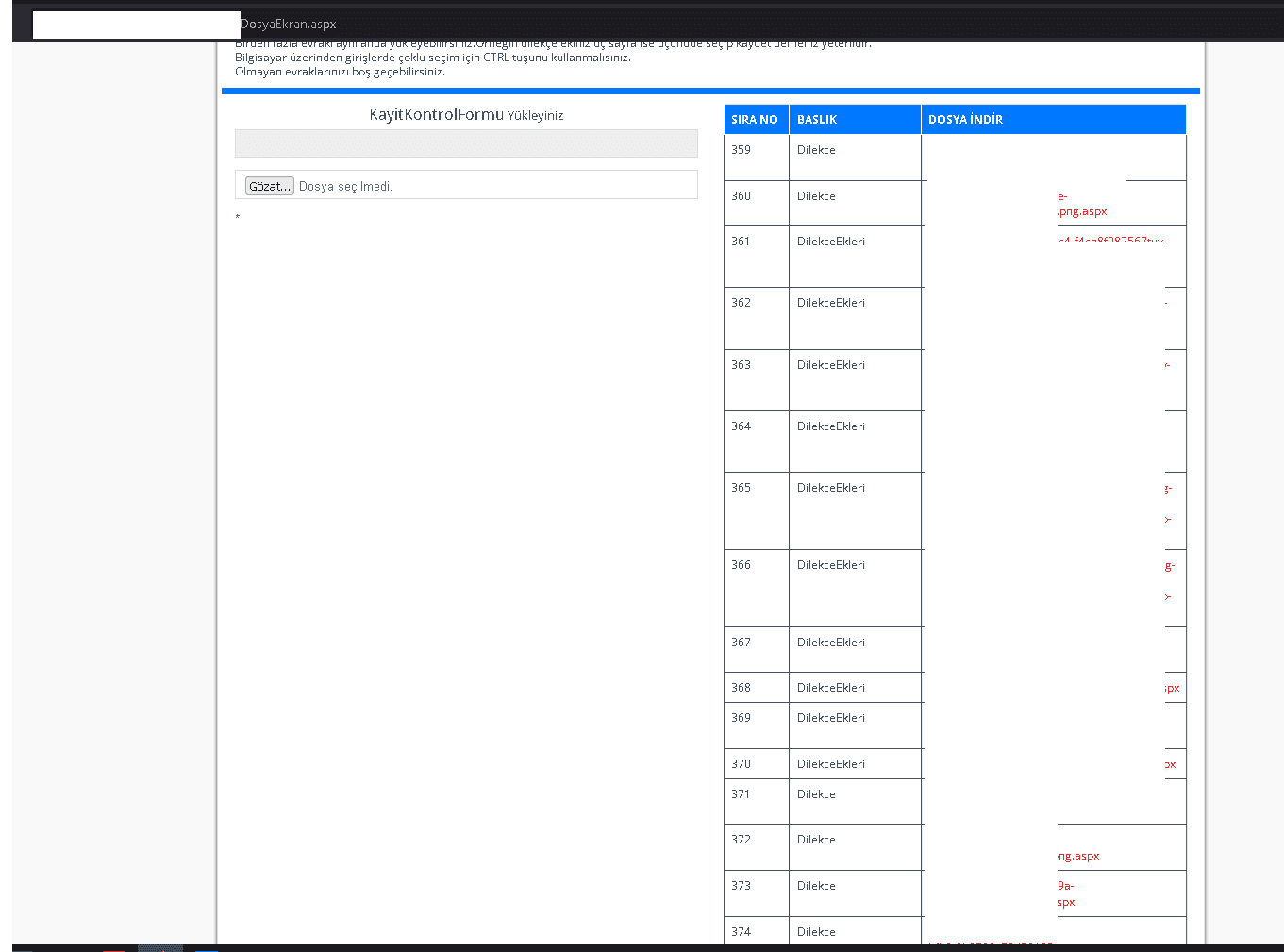
After seeing this form, one question came to our minds… This question is: Can files with different extensions be uploaded other than docx, pdf, jpg files sent in the form? We were wondering if the system was checking the extensions. After making the necessary requests with Burp Suite, we realized that there was no extension control and we uploaded our malicious file to the system.
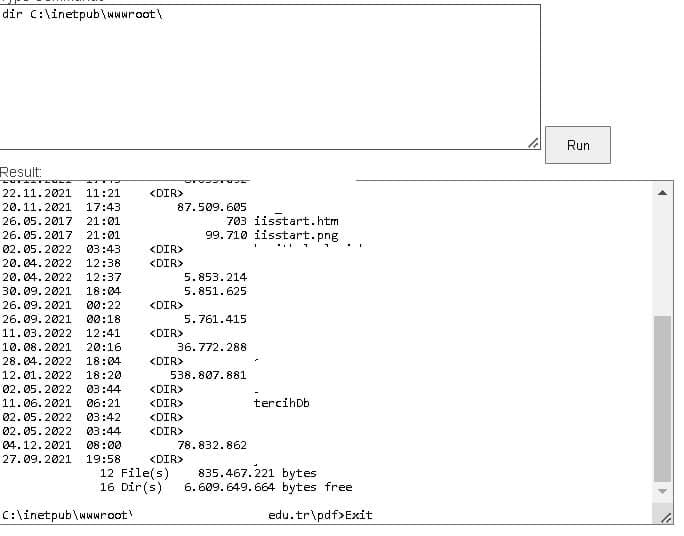
The fact that the application running on the system was running with the “NT AUTHORITYSYSTEM” privilege was a bigger mistake to learn from.
A reverse shell connection was made to the server to which the shell was thrown, and a sqlcmd connection was made via the command line. The sqlcmd configuration was open, however, it was directly redirected to the database without asking for any login information, another step that showed how critical the security was for the internal network. Attackers who follow their reconnaissance methods rationally can infiltrate target structures with seemingly insignificant arguments and steal critical information from your systems.In addition, the recent increase in ransomware is among the strongest possibilities due to money-motivated attackers. See you in our next article as the Secunnix team.


