What is this Pegasus?
In today's article, we will examine phone spyware that is closely related to many countries and will help us understand the point of spyware today. The first spyware we will examine will undoubtedly be “Pegasus”. It is a spying program developed for remote monitoring. The software aims to seize the targeted person's features such as message, location, microphone, etc., and to gather intelligence for the countries that buy them. We would like to underline the word countries here. We will address this point later.

How does Pegasus work?
In the oldest version of Pegasus, which was seized by security researchers in 2016, the method used to infect the targeted person's phone is recorded as phishing. In other words, a link is shared that the targeted person has to click to infect his phone with malware. This link is social engineering. By combining them, the attack is carried out by increasing the click probability of the target.
In later versions, NSO Group's attack capabilities are further improved. We see this improvement with the 0-Day vulnerabilities they found on applications. There is no need to share a link for the target anymore. With 0-Day on the found application, the attack occurs and the targeted person is attacked. The group, who discovered 0-Day in applications such as WhatsApp and iMessage, which are the most popular today, could infiltrate the targeted person with a phone call on Whatsapp (it doesn't matter whether the target picks up the phone or not) or a message sent via iMessage (it doesn't matter whether the target reads the message or not).
The smartphone market, which mostly uses Android and IOS operating systems, could not find a solution for this spyware? Actually, it is not very easy to extract the information obtained from the targeted phone. Because at this point you can get stuck in some security stages of the operating system. The easiest way is to use “Root(privilege)” if the target phone is Android, and “Jailbreak” if the IOS is in. At this point, the following question should come to mind: “For a group that discovers 0-Day vulnerabilities in applications such as WhatsApp, iMessage, the operating system should use Local Root Exploit or How hard can JailBreak be to write? It doesn't seem like that hard
Even if it is difficult, the last resort may be to ask the user for the necessary permissions to extract the data.
States and Pegasus
States, intelligence agencies, the rich… Who are Pegasus' customers?
Pegasus is not sold to companies or individuals, but only to intelligence services and governments. All sales of the company must be approved by the Israeli Ministry of Defense. As soon as the program enters five countries (USA, China, Russia, Israel, Iran) at the request of the Israeli government, it will self-destruct allegedly.
Of course, all of the above is a claim…After all, it does not show us that it does not sell to companies or individuals. We know that more than 1000 people in 50 countries have been targeted by NSO customers since 2016. These targets include 189 journalists, more than 600 politicians. According to reports, there are several heads of state, including French President Emmanuel Macron, South African President Cyril Ramaphosa, and Pakistani Prime Minister Imran Khan.
Journalists include employees of Al Jazeera, The Associated Press, Reuters, CNN, The Wall Street Journal, Le Monde and The Financial Times. At least 65 corporate executives and 85 human rights activists worldwide were also targeted. Saudi Arabia There are allegations that Hatice Cengiz, the fiancee of Cemal Kaşıkçı, who was killed in the Saudi Consulate General in Istanbul, and his close friend Ömer Abdülaziz, and İrfan Fidan, who was the Chief Public Prosecutor of Istanbul during the Khashoggi investigation, were among those followed. , Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia and the United Arab Emirates” is another information that is the subject of the reports.
Is Türkiye targeted?
According to published reports, there have been people targeted from Turkey. Turkish Journalist Turan Kışlakçı, President of the Turkish-Arab Media Association, is one of the targeted people. Some of the domains that Pegasus software uses to transfer information from the targeted phone to the control center,
- https://turkeynewsupdates.com/
- https://turkishairines.info/
Based on these domains, it is believed by our team that many people were affected by these attacks.
What was the reaction despite the reports?
In a statement released after the report's publication, Agnes Callamard, Amnesty International's Secretary-General, denied allegations that NSO's technology was used for law enforcement purposes. which Pegasus is also the preferred spyware for those who want to spy on foreign governments.” In July 2021, the Paris prosecutor's office launched an investigation into allegations that Moroccan intelligence services were spying on several French journalists. Morocco denied the allegations. Last November, the US Department of Commerce, NSO Group blacklisted and denied access to US technology. NSO denied abuse of power and said it did not identify its customers. It claims that its products are designed for use against criminals and terrorists and that it sells its products only to state security agencies with the approval of the Israeli defense ministry.
How can I tell if I have Pegasus on my phone?
While you are reading this article, maybe you are a target, maybe Pegasus is active on your phone right now. We will share some information for you to understand this, relatively easy way to detect it, you can use Amnesty International Mobile Verification Toolkit. https://github.com/mvt -project/mvt This tool can run under both Linux and MacOS and can analyze your mobile device's files and configuration by analyzing a backup taken from the phone.
Is it possible to be protected from Pegasus?
There is currently no up-to-date solution for 0-Day attacks, but some measures are possible for Pegasus and other spyware.
- Current operating system versions should be preferred,
- You can allow domain names and IPs that you trust with the help of a firewall at the point of your phone accessing the Internet. (The most effective solution),
- Restarting your phone for iOS operating systems will fix the reboot problem even if Pegasus Spyware is active,
- Do not connect to unsafe internet hotspots such as Free Wifi, Public Wifi, Hotel Wifi
- Use VPN,
- Do not click on links that you do not know the source,
- Restrict app permissions,
- Do not install applications that you do not know and do not trust.
Predator Spyware
After examining Pegasus Spyware, the name of our second spyware we will examine: Predator Spyware. It is a spyware developed by Cytrox Software from North Macedonia. It is up to you, our readers, to decide whether this spyware, which is as effective as Pegasus, is more dangerous than Pegasus. Because in the analyzes made to date, there are some points where Predator is more dangerous. The most important of these is that Predator can continue to work after a reset in the IOS operating system. The most important factor that distinguishes Predator from Pegasus and makes it more dangerous is IOS the ability to run itself even after restarting the phone in the operating system.
Cytrox company describes itself as a Cyber Intelligence Solutions company that provides governments to collect information from devices and cloud services. Today, the number of companies producing such solutions is increasing day by day. continues to pose a threat to countries. As Secunnix, our prediction is that the increase of these companies is actually a show of strength in preparing their countries for cyber wars. We should not forget that in the Russia-Ukraine war, before the war started, Russia started an attack on Ukraine's internet infrastructure. Does Turkey have such preparations? As a result of our analyzes, we have been working on taking precautions against such attacks as a country, but companies that will carry out similar studies have not been formed yet. As Secunnix, we care about these issues, constantly examine them, and work on these issues. We are also stating the good news that we will start very soon through our article.
What are the differences between Pegasus and Predator?
Predator is a little weaker than Pegasus in the field of R&D. This is because Pegasus is working with 0-Day vulnerabilities it found, while Predator is trying to take advantage of more public vulnerabilities. The most important of these is CVE- The vulnerabilities were 2021-37973, CVE-2021-37976, CVE-2021-38000, CVE-2021-38003 and CVE-2021-1048 on Android.The software was trying to settle on the target's phone over a connection using them.Citizenlab's Predator specific We will share a few screenshots from the analysis of the targeting of Ayman Nour, an ex-Egyptian politician and journalist living in Istanbul in his work. These images are related to the links directed to the target.
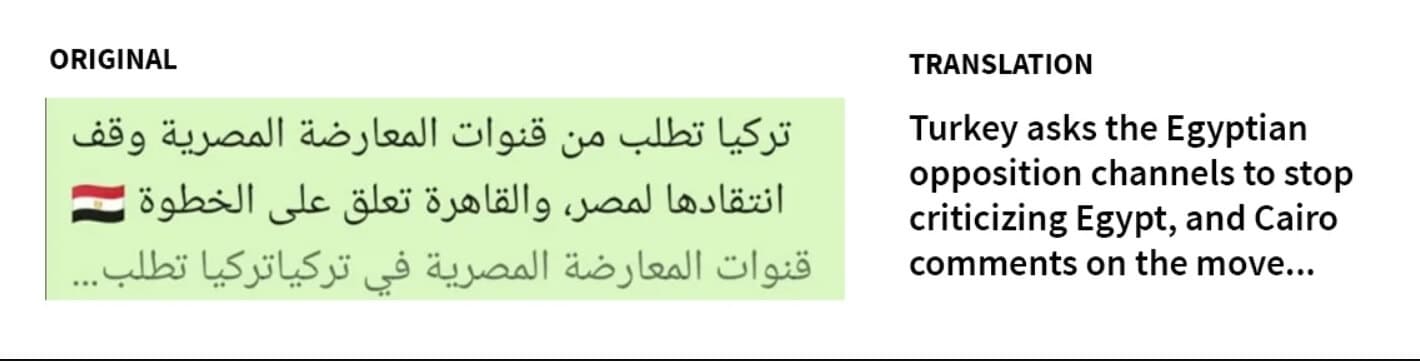
An accompanying image to the Cytrox Predator link sent to Nour: Turkey asks Egyptian opposition channels to stop criticizing Egypt and is commenting on Cairo...
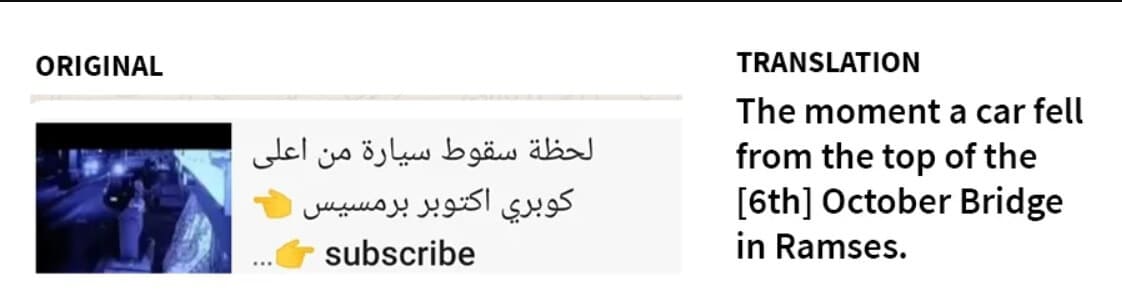
An accompanying image to a Cytrox Predator link sent to Nour: The moment a car fell from the top of the [6th] October Bridge in Ramses.

An accompanying image to the Cytrox Predator link sent to Nour claims to be a link to the legal website of the newspaper Al Masry Al Youm. The real link goes to the fake almasryelyuom[.]com.
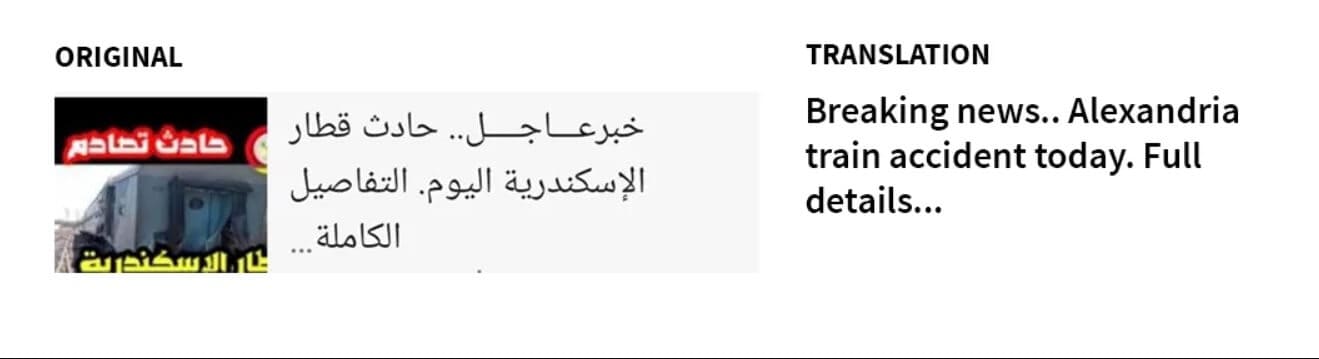
An accompanying image to the Cytrox Predator link sent to Nour: Breaking news.. Alexandria train crash today. All details...
As you can see, the target person's phone is being attempted to be seized over various connections.
Current Predator attack
Although these software are the subject of constant reports, it should not be forgotten that they still continue to work actively, and companies are constantly working to find different methods. Finally, on July 27, Greek socialist leader Nikos Androulakis to the Supreme Court Prosecutor's Office; Using Predator spyware, filed a complaint stating that he had attempted to wiretap his cell phone.
We felt it necessary to leave this note because we thought it was important. Although Cytrox, the producer of Predator, appears to be a North Macedonian company, it should be noted that it was acquired by different Israeli consortia. Cytrox Software is also an Israeli company like NSO Group.


