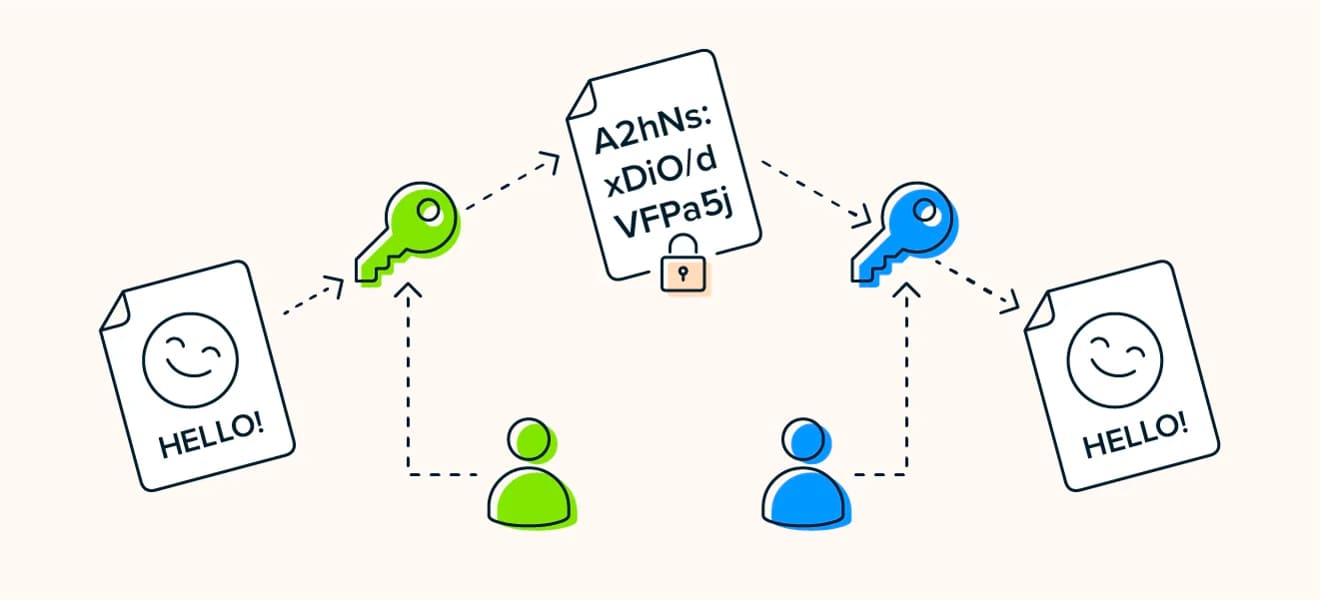
Hive ransomware, first seen in June 2021, has begun to spread again, this time in an unprecedented form. Hive developers, who used the Golang in their previous versions, seem to have shifted the programming language selection to Rust in their new versions. The most important reason for this choice is that the Rust language makes reverse engineering studies very difficult. As a result of the use of the Rust language, the size of the ransomware’s functions increases to quite large levels. This means that the analyst spends much more time and effort examining the ransomware. The new Hive version, which works with a different username and password information for each attacked target, seems to have taken this tactic from the BlackCat ransomware group. Previously, ransomware stored this information within itself. In this way, the user name and password could be captured by the analysts. In this version, the username and password information is given as a parameter to the malware instead of being embedded in the malware. Thanks to this approach, analysts who get the malware cannot find out where the target is.
Apart from the change in programming language, the Hive team seems to be following the trail of ransomware they wrote in Golang. The first time Hive runs, it first raises its authority level. In order to do this, it tries to steal the authorization level of some processes with high authorization level running in the system. It then stops some services and programs running on the system.

Scanning the file system via the Windows API
Thanks to this stopping process, it is possible to prevent Hive from being caught by some anti-malware applications and to cause loss if it is encrypted in the system. Some process has been stopped. If these process are in working condition, Hive will not be able to access the files it wants to encrypt, so it stops these programs before it starts scanning the file system. Because the encryption mechanism is similar to that of previous versions, Hive allows files to be encrypted. Two 13MB master key files are created to be used during the process. Then, the fixed and removable disks in the system; at the same time, if it is specified with the parameter, it scans the network share directories that are active in the system.

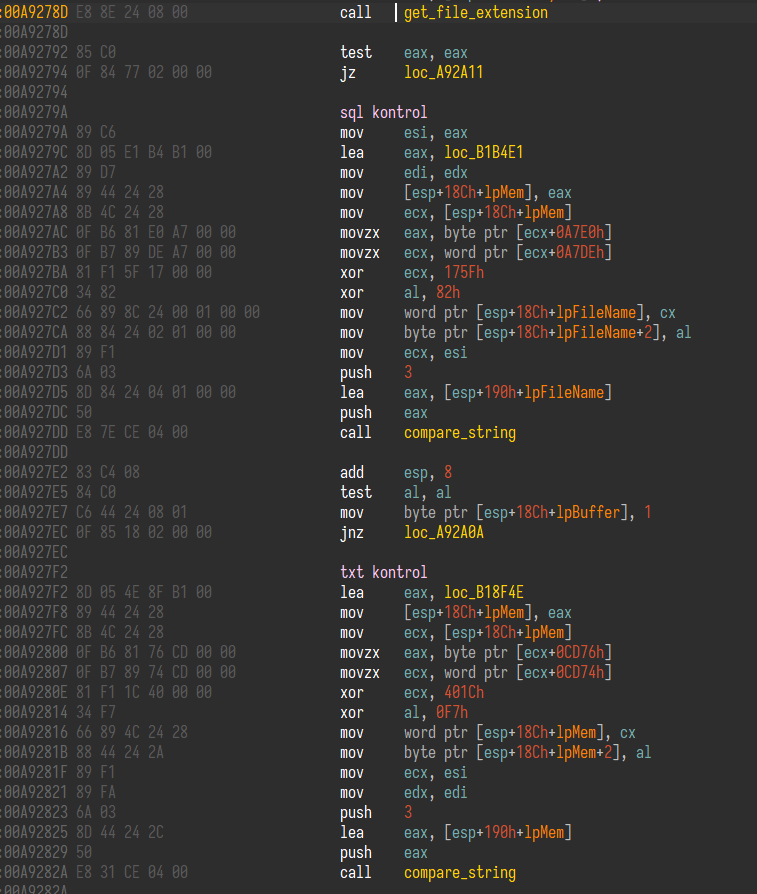
Checking the extensions of the files to be sent to the server for the threat of leakage
Hive, discovering the file system, encrypts files that meet certain criteria, similar to the previous version of Go. During this encryption process, some files that may contain valuable information such as sql, txt, rtf, doc, xls are sent from the computer to servers by Hive. In this way, Hive ransomware actors use the leaking of valuable information as a threat if the target does not pay the ransom.
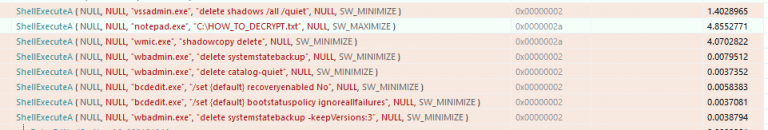
The final step
Hive deletes files and system backups by running some commands on the system, as many other ransomware do, to make file recovery difficult. Finally, it opens a notepad application and displays the ransom message so that the target can understand that the system has been encrypted.

Hive Ransomware C&C Server List
http://209.133.223.69/
http://37.72.172.110/
http://23.227.190.216/